This rabbit is not innocent, it's "bad".
At a time when the world has been witnessing an increasing number of ransomware attacks crippling computer systems across the globe, a new malicious software campaign has hit several Eastern European countries, and is now spreading elsewhere. Dubbed "Bad Rabbit", the new malware is believed to be a possible variant of the notorious Petya (or ExPetr) ransomware.

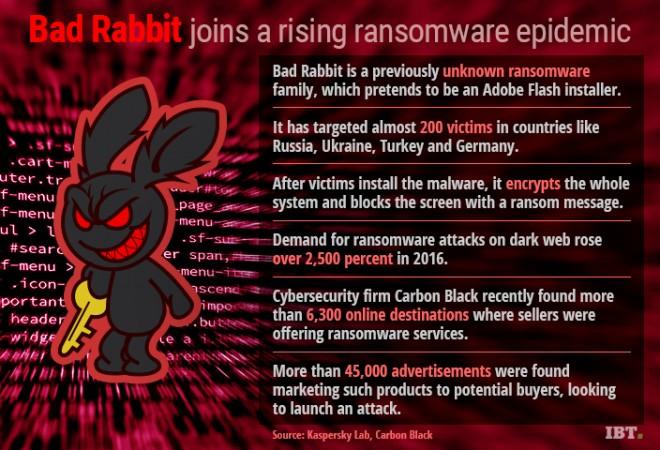
The "Bad Rabbit" ransomware, which has so far affected 200 targets in multiple countries, asks for 0.05 Bitcoin – which equals to about $271 or Rs. 17,689 at the current exchange rate -- as ransom in return for encrypted data.
"This ransomware has infected devices through a number of hacked Russian media websites. Based on our investigation, this is a targeted attack against corporate networks, using methods similar to those used in the ExPetr attack," Alex Perekalin of Kaspersky Lab said in a blog post.
Here're a few important things to know about the Bad Rabbit ransomware, which is considered as the third ransomware attack to hit systems this year, after the infamous WannaCry and Petya in May and June, respectively.
1. Bad Rabbit is a previously unknown ransomware family, and it is distributed through drive-by attacks in which the target, while visiting a legitimate website, downloads the malware disguised as an installer.
2. The Bad Rabbit malware dropper pretends to be an Adobe Flash installer. The downloaded file is named install_flash_player.exe, which needs to be manually launched by the victim.
3. Once the fake flash installer is executed, it drops an encryptor file called C:Windowsinfpub.dat and uses the command C:Windowssystem32rundll32.exe to execute the malware and continue the malicious operations.
4. The infpub.dat file also installs the malicious executable dispci.exe -- apparently derived from the code base of the genuine utility DiskCryptor -- into C:Windows and creates a task to launch it.
5. The malware also creates another scheduled task that is responsible for rebooting the system.
6. Bad Rabbit ransomware creators have used names of various Game of Thrones characters to refer to strings used throughout the source code.
7. The ransomware sets up three scheduled tasks named Drogon (shuts down the victim's machine), Rhaegal (executs the decryptor file) and Viserion (reboots the target system a second time) -- the names of the three dragons from Game of Thrones.
8. The ransomware asks victims to access a site on the Tor network to make pay the ransom.
9. Based on the ransom note, victims have just over 40 hours to make the payment before the ransom fee goes up.
10. It's still unknown whether it's possible to retrieve files encrypted by Bad Rabbit, either by paying the ransom or by exploiting some glitch in source code.

















