After witnessing cyber attacks of WannaCry and Petya (aka ExPetr), a new deadly ransomware dubbed Bad Rabbit is on the prowl affecting government, corporate and media houses of Russia, Ukraine, Bulgaria, Germany and some eastern European regions.
Affected victims are reporting that the Bad Rabbit creators are asking 0.05 Bitcoin (approx. $271/€231/Rs. 17,689) as ransom in return for encrypted PC data.
Bad Rabbit Origin:
As per Kaspersky Labs, Bad Rabbit spreads through drive-by attacks similar to the Petya ransomware and is said to be targeting mainly corporate and media (or news) websites' networks.
How Bad Rabbit ransomware infiltrate target computers?
Bad Rabbit is said to be using sophisticated techniques to avoid detection and what's more frightening is that victims are lured to download fake Adobe Flash installer application from legitimate websites.
Also read: nRansomware demands your nude photos to recover locked files
Naive unsuspecting users install the malware onto their PCs and hackers encrypt the whole system and block the screen with ransom message [See below].
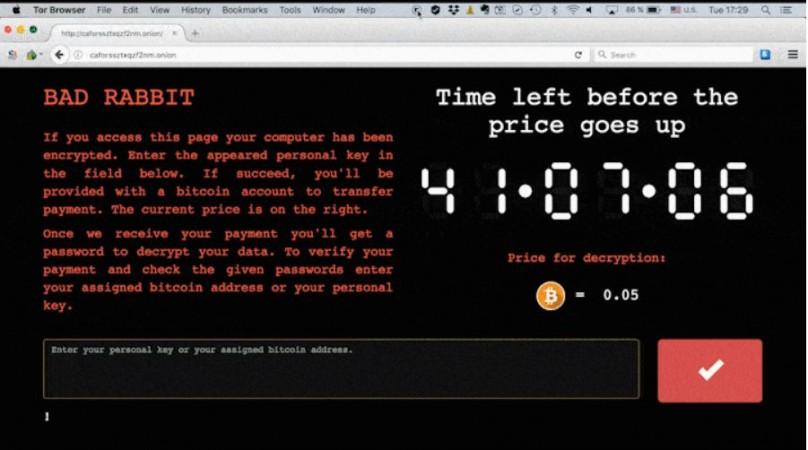
Should you be worried about Bad Rabbit?
Well, Kaspersky Labs claims that the Bad Rabbit has affected 200 targets in multiple countries, but it is slowing down. But, so far, there is no solution to recover the data from the affected system.
Hence, users are advised to exercise caution even when downloading a legitimate software and should immediately install anti-virus applications. Also, follow the steps below to be safe from Bad Rabbit ransomware.[As recommended by Kaspersky Labs]
- Block the execution of files c:windowsinfpub.dat and c:Windowscscc.dat.
- Disable WMI service (if it's possible in your environment) to prevent the malware from spreading over your network.
Here's how to protect your PCs from ransomware and malware:
- Always keep your PCs updated with the latest firmware; most software companies including Microsoft and Apple usually send software updates regularly in terms of weekly or monthly and make sure to update them immediately
- Make sure to use premium Anti-virus software, which also provides malware protection and Internet security
- Never open email sent from unknown senders
- Disable ActiveX content in Microsoft Office applications such as Word, Excel, etc.
- Disable Remote Desktop Connections, employ least-privileged accounts. Limit users who can log in using Remote Desktop, set an account lockout policy. Ensure proper RDP logging and configurations
- Never install plugins (for browsers) and application software on the PCs from un-familiar publishers
- System administrators in corporate companies should establish a Sender Policy Framework (SPF) for their domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
Additional security measures that may be considered by system administrators:
- Use RDP Gateways for better management
- Change the listening port for Remote Desktop
- Tunnel Remote Desktop connections through IPSec or SSH
- Two-factor authentication may also be considered for highly critical systems



![Ultrahuman launches Ring PRO, free charging case with more than just power and Jade AI [details] Ultrahuman launches Ring PRO, free charging case with more than just power and Jade AI [details]](https://data1.ibtimes.co.in/en/full/829151/ultrahuman-launches-ring-pro-free-charging-case-more-just-power-jade-ai-details.png?w=220&h=135&l=50&t=40)











![Ultrahuman launches Ring PRO, free charging case with more than just power and Jade AI [details]](https://data1.ibtimes.co.in/en/full/829151/ultrahuman-launches-ring-pro-free-charging-case-more-just-power-jade-ai-details.png?w=220&h=135)

