The unprecedented rise and the equally unpredictable falls in cryptocurrency prices, including that of Bitcoin, may have made many overnight millionaires, but as progressive as they may seem, these digital currencies are prone to many attacks.

And just as the world is trying to come to terms with the nitty-gritty of the cryptocurrency game, and get over the WannaCry ransomware attack another new cryptocurrency malware seems to have hit millions of Android devices which are reportedly being "cryptojacked" in a drive-by cryptocurrency mining campaign.
Also read: What is cryptojacking? Cryptocurrency mining malware hits thousands of US and UK government websites
According to Malwarebytes, millions of Android mobile users have been redirected to a specialized page "performing in-browser cryptomining."
The report also reveals that this is one of the biggest operations that is being targeted only at mobile users.

As per the security researchers, hackers have been secretly mining Monero coins via Android smartphones over the past few months. The campaign was first observed in January 2018, though it had started sometime around November last year.
More than 60 million visitors have already visited the malicious domains, according to the report.
The Modus Operandi
The report suggests that the method used by the hackers is "automated, without user consent, and mostly silent." And although it is still not clear what exactly is the method used, it appears that users, or rather victims, downloaded some infected apps that redirect them to the specifically designed host website.
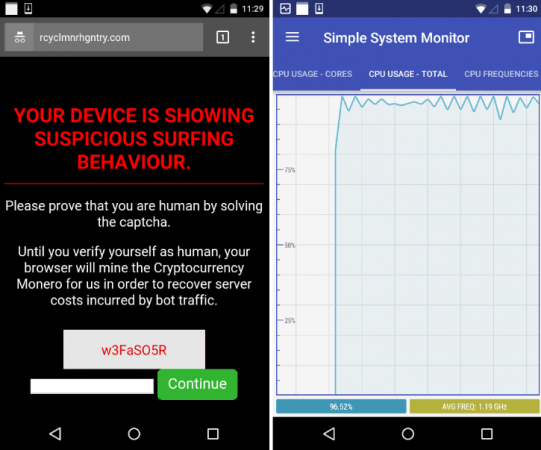
Once the users are redirected to the malicious page they are asked to solve a CAPTCHA to prove that they are human and not a robot.
The website clearly mentions that it will be using the infected device to mine cryptocurrency and would only stop when the user enters the CAPTCHA code.
The warning message displayed reads: "Your device is showing suspicious surfing behaviour. Please prove that you are human by solving the captcha. Until you verify yourself as human, your browser will mine the Cryptocurrency Monero for us in order to recover the server costs incurred by bot traffic."
Until the user does not enter the CAPTCHA code, the smartphone continues mining Monero for the hackers, thereby damaging the device's processor in the process.
Interestingly, upon entering the code, users are redirected back to Google homepage, the report says.
Malwarebytes has shared the screenshot of the site and the resulting processor damage when the malware hits.
"It's possible that this particular campaign is going after low-quality traffic, but not necessarily bots, and rather than serving typical ads that might be wasted, they chose to make a profit using a browser-based Monero miner," Jerome Segura, lead malware intelligence analyst at Malwarebytes, wrote in the blog post.
Malwarebytes has identified five domains that use the same CAPTCHA code and Coinhive site keys used for the campaign.
According to the researchers, at least two of the websites had more than 30 million visits per month and all domains combined, yielded around 800,000 visits per day, with a visitor spending an average four minutes on the site. Now, this may have allowed the hackers to mine a lot of Monero coins but the report does not specify how much.
"It is difficult to determine how much Monero currency this operation is currently yielding without knowing how many other (malicious) domains are out there. Because of low hashrate and the limited time spent mining, we estimate this scheme is probably only netting a few thousand dollars (worth of cryptocurrency) each month. However, as cryptocurrencies continue to gain value this amount could easily be multiplied a few times over," the report states.
Malwarebytes highly recommends users use web filters and security apps to keep malware attacks at bay and prevent such hijacks. The researchers warn that nowadays forced cryptomining is affecting mobile phones and tablets not only via Trojans in apps but also via redirects and pop-ups. So, it's always safe to avoid any apps from unknown develops and from app downloading sites.















