
Millions of computers around the world are at the risk of being infected by a massive new ransomware attack. According to security researchers, the malicious software is being distributed by Necurs, which is claimed to be the world's largest botnet, through millions of spam emails.
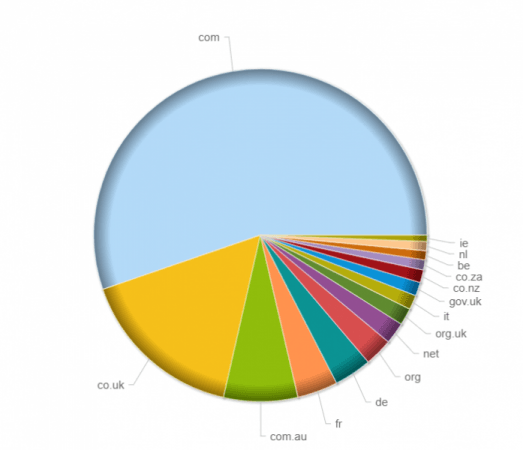
The Scarab ransomware, which was first spotted on November 23, is primarily being sent to .com email addresses, followed by region-specific top level domains (TLDs) for the United Kingdom, Australia, France and Germany. The ransomware was delivered to as many as 12.5 million email addresses in just the first six hours of the attack, according to Forcepoint, an anti-virus software company based in Austin, Texas.
The spam emails in question use the subject line "Scanned from {printer company name}" and contain a 7zip attachment with a VBScript downloader. To make the scam messages look legitimate, the attackers hide the infected files inside fake scanned documents that are apparently created using printers from reputed companies like Lexmark, HP, Canon and Epson.
Once the attached 7zip is downloaded and opened, the Scarab ransomware takes over the infected computer and threatens to destroy files if a Bitcoin ransom is not paid.
"Once installed it [the ransomware] proceeds to encrypt files, adding the extension '.[suupport@protonmail.com].scarab' to affected files. A ransom note with the filename 'IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT' is dropped within each affected directory. The misspelling of 'support' is present in both the modified filenames and the ransom note, and is presumably a result of the availability of email addresses on the Protonmail service," Forcepoint said in a blog post.
The note, however, doesn't specify the exact ransom amount. Instead, it says that "the price depends on how fast you write to us."
The attackers behind the Scarab ransomware have set email as the primary communication mechanism. However, since it can be an unreliable tactic if email service providers quickly shut the domain down, the attackers have also given a secondary BitMessage contact.

"By employing the services of larger botnets such as Necurs, smaller ransomware players such as the actors behind Scarab are able to run a massive campaign with a global reach," Forcepoint said. "It remains a question whether this is a temporary campaign, as was the case with Jaff, or if we will see Scarab increase in prominence through Necurs-driven campaigns."
Jaff was a new ransomware that was spread by the Necurs botnet using a malicious email campaign in May.
The best way to avoid being infected by a malware email is to never open an unwanted attachment. Archive files, like the 7zip format used in the Scarab ransomware attack, should also be considered as a sign of potentially dangerous content as such type of files can be used to bypass anti-virus scans.
In addition, it's always recommended to have a data backup either via cloud storage or an external storage device that is not always connected to the computer.









