India has largely remained insulated so far from the massive ransomware attack that started in Ukraine and Russia on Tuesday and was spreading to other parts of world, including Asia, on Wednesday, IT Minister Ravi Shankar Prasad has said.
"We have been taking proactive steps... we have sent out advisories (on the cyber attack and the malware)... India is not much affected at this stage," Prasad said here.
He was speaking at the inauguration of the two-day National Convention on 'Digitalization: Opportunities and Challenges'.
The Shipping Ministry on Wednesday said operations at one of the container terminals at Mumbai's Jawaharlal Nehru Port Trust (JNPT) were impacted due to a global cyber attack.
According to the Ministry, a private terminal operator at the JNPT was taking steps to address the issue.
It was anticipated that there could be bunching of in-bound and out-bound container cargos.
"An unforeseen situation has developed at the JNPT owing to disruption in the operations of one of the private terminal operator, APM Maersk," said a Ministry statement.
"It has been informed by the private terminal operator that this disruption is a consequence of a worldwide disruption being faced by them because of a cyber attack," it added.
The Ministry said the JNPT was taking steps to ensure minimum disturbance to trade, transporters and local citizens.
Industry lobby Assocham, however, said that the halting of the container movement at the JNPT, following the global cyber attack, is a big warning as to how India is actually no more insulated from such deadly computer viruses which are unleashed to hit the lifeline of the economy.
"The Assocham would urge the government to take a lead in forming a powerful global alliance which could immediately swing into action on a world wide basis, the moment such computer viruses are released for playing havoc," Secretary General D.S. Rawat said in a statement.
The government is keeping close watch on the issue, Prasad said.
Cyber security experts believe that the new attack was caused by a variant of the Petya ransomware which was unleashed in 2016.
It exploits the same vulnerabilities in Windows systems that WannaCry, the ransomware that affected 200,000 people in 150 countries in May, exploited.
American computer security software company McAfee has warned that the current attack could be a test run for a much bigger and bolder attack in the future.
"We believe that today's events are part of the natural evolution of ransomware technology, but also a test run for a much bigger and bolder attack in the future," Anand Ramamoorthy, Managing Director, South Asia, McAfee, told IANS.
"WannaCry took advantage of a vulnerability in Microsoft Windows, along with an exploit that enabled it to not only spread through a worm technique, but also encrypt files and demand a ransom from its victims. The unique element of Petya is that it builds on the worm-based technique that WannaCry established and added a new element that allows non-vulnerable machines to become infected as well," Ramamoorthy explained.
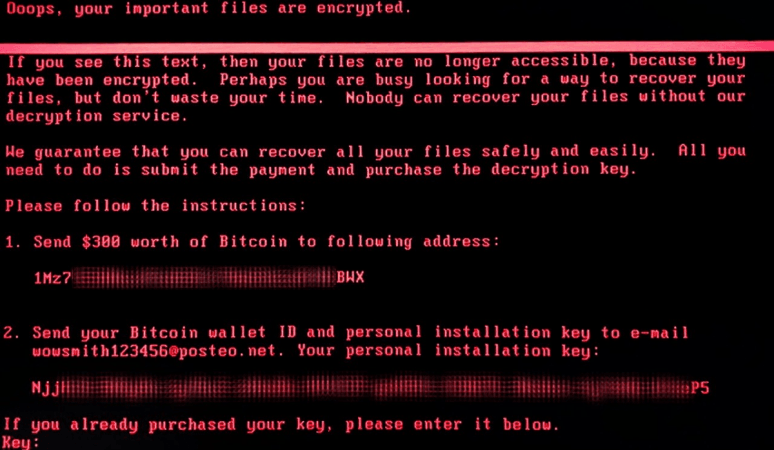
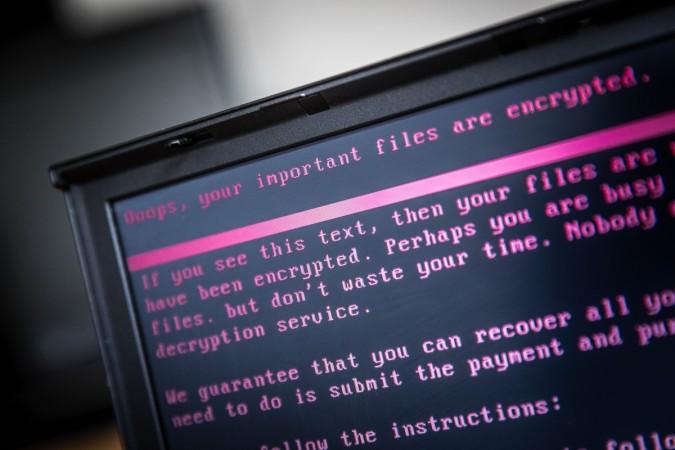
In this latest attack, a ransom note is displayed on infected machines, demanding that $300 in bitcoins be paid to recover files, Symantec Corporation, one of the global leaders in cyber security software, said.
"Petya has been in existence since 2016 and differs from typical ransomware as it doesn't just encrypt files, it also overwrites and encrypts the master boot record (MBR). One of the methods Petya uses to propagate itself is by exploiting the MS17-010 vulnerability, also known as Eternal Blue," said Tarun Kaura, Director- Product Management, Asia Pacific Japan, Symantec, one of the global leaders in cyber security software.
The attack in Ukraine, which had been the country initially most damaged by this cyber attack, has been halted, according to an Efe new report.
Earlier, a Ukrainian federal agency said that the automatic radiation monitoring system at the Chernobyl nuclear power plant had been hit by the cyber attack and monitoring was being carried out manually.
But the situation is now "under the full control" of cybersecurity specialists who are working to recover lost data, the government said.
Cyber security experts are not sure who is behind the attack. Ukraine earlier pointed the finger to Moscow for everything, despite the fact that there are several Russian state-owned companies and banks among the victims as well.
US pharmaceutical giant Merck, the world's second largest such firm, confirmed on its Twitter account that its computer network was compromised on Tuesday in the global attack.
The attack also affected Denmark's Maersk shipping company and the French glassmaking and construction materials giant Saint-Gobain.

















![Nothing to open its first global flagship store in THIS Indian city [details]](https://data1.ibtimes.co.in/en/full/827007/nothing-open-its-first-global-flagship-store-this-indian-city-details.png?w=220&h=135)