
A massive ransomware cyberattack, which is believed to have originated from cyber weapons developed by the US National Security Agency (NSA), has infected systems in hospitals across England and hit Spanish telecommunications company Telefonica. The ransomware, known as "WanaCrypt0r 2.0" (aka WannaCry or WCry) has spread to nearly 100 countries with 75,000 detections found so far.
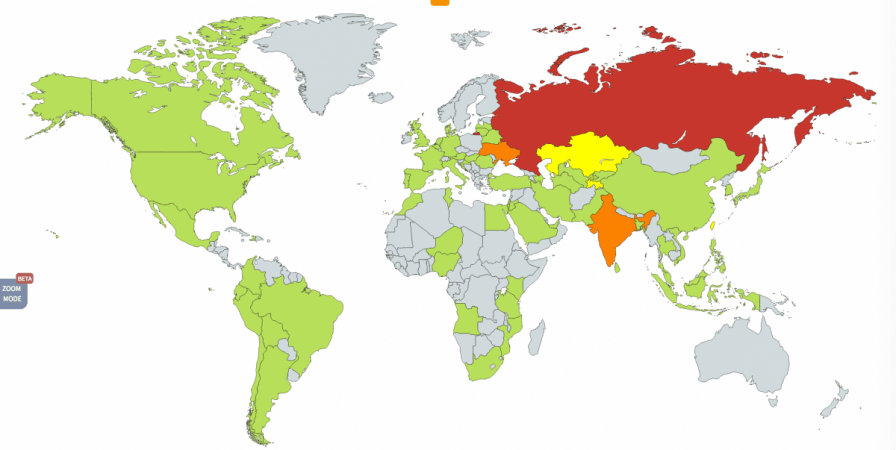
According to security software maker Avast, the ransomware was mainly targeted at Russia, Ukraine and Taiwan, but it turned into a global havoc, contaminating systems across the world. Security researchers with Kaspersky Lab said that they have recorded attacks in 99 countries, including India, China, Italy and Egypt.
Security researchers at Malware Hunter Team said that the ransomware had spread to the United States and South America by Friday evening while Europe and Russia remained the ones to be hit the hardest. According to the Russian interior ministry, WannaCry infected nearly 1,000 computers in the country.
Here's a map that shows the countries being targeted most by WanaCrypt0r 2.0, which is now available in 28 different languages, including Bulgarian and Vietnamese:
The ransomware can change the affected file extension names to ".WNCRY". Therefore, an infected file will look something like: original_name_of_file.jpg.WNCRY. Even the encrypted files are also marked by the "WANACRY!" string at the beginning of the file, according to a note issued by Avast.
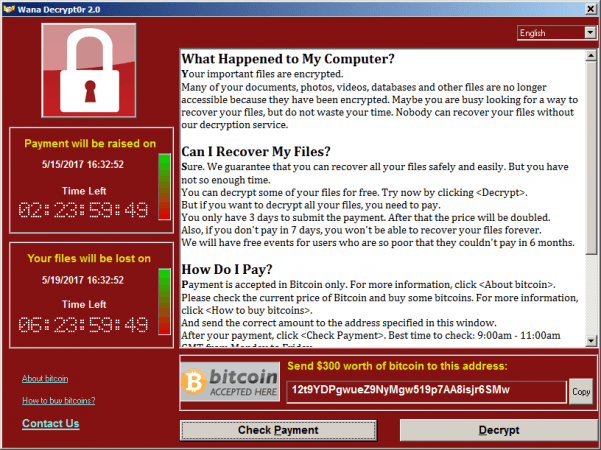
The ransomware demands payments of $300 to $600 to restore access. Some security researchers have observed victims paying the ransom via the digital currency bitcoin. The message dropped by the cybercriminals behind Wana Decrypt0r 2.0 includes instructions on how to pay the ransom, an explanation of what happened and a countdown timer.
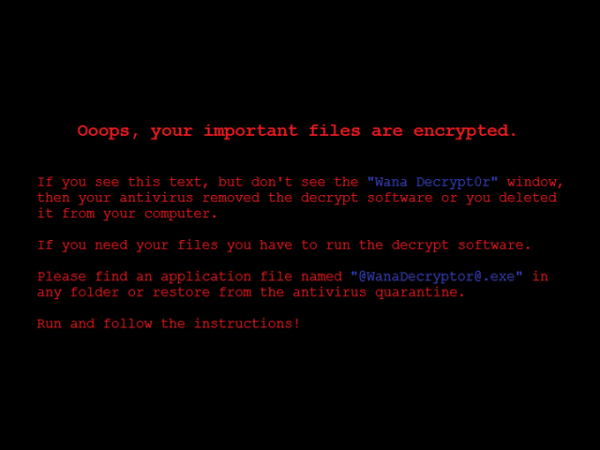
In addition, the wallpaper on the victim's computer gets changed to display the following image:
A hacker group called Shadow Brokers reportedly released the malware on April 14. It was the same group which claimed last year to have stolen a cache of "cyber weapons" from NSA.
According to Kaspersky Lab, the WannaCry ransomware attack was initiated through a remote code execution in Microsoft Windows. Although Microsoft patched the exploit on March 14, many organisations have not yet installed the patch.
Meanwhile, whistleblower Edward Snowden took to Twitter to blame the NSA for mayhem.
If @NSAGov had privately disclosed the flaw used to attack hospitals when they *found* it, not when they lost it, this may not have happened https://t.co/lhApAqB5j3
— Edward Snowden (@Snowden) May 12, 2017
On Friday, the US Department of Homeland Security said in a statement that it was aware of the ransomware attack, and that it was "actively sharing information related to this event" with domestic and foreign partners.
The department also said that it was "ready to lend technical support and assistance as needed to our partners, both in the United States and internationally."

















