
A little over a month after the deadly WannaCry ransomware hit global cyberspace, a new threat dubbed as the 'ExPetr' (aka Petya aka NotPetya aka Goldeneye) has emerged, and is spreading rapidly across the world. ExPetr, which was first detected in Ukraine a few hours ago, has spread to major corporate companies in Russia, US, UK, Germany, France, India, Italy, Spain and Poland, among other countries. It has reportedly affected 2,000 users so far.
Is ExPetr more dangerous than WannaCry?
Initial reports indicate that ExPetr is behaving like WannaCry and uses the same US goverment-run NSA (National Security Agency)'s leaked 'EternalBlue' exploit. Once it gets inside the system, its encrypts the entire information and asks for a ransom amount of $300 in bitcoins to get access to the computer.
However, leading computer security firm Kaspersky Lab says that ExPetr is more complex as compared to WannaCry, as it uses numerous vector points of compromise to affect the system. What's more worrying is that, no one has found a kill switch for the ransomware, yet.
It also warned that a single infected system on the network possessing administrative credentials is capable of spreading it to all the other computers through WMI (Windows Management Instrumentation) or PSEXEC.
[Note: PSEXEC is a command-line tool that lets a user execute processes on remote systems and redirect console applications' output to the local system so that these applications appear to be running locally.]
Sample .exe files used in the ExPetr ransomware attack (for System Administrators)
- Trojan-Ransom.Win32.PetrWrap.d
- HEUR:Trojan-Ransom.Win32.PetrWrap.d
- PDM:Trojan.Win32.Generic
- UDS: DangerousObject.Multi.Generic
- Intrusion.Win.MS17-010.e
Security measures to prevent malware attack (courtesy Kaspersky Lab):
- Make sure all protection mechanisms are activated as recommended by the anti-virus/malware software and also check KSN (Kaspersky Security Network) and System Watcher components (which are enabled by default) are not disabled.
- Configure and enable the Default Deny mode of the Application Startup Control component of Kaspersky Endpoint Security to ensure and enforce the proactive defence against ExPetr and future attacks.
- As an additional measure, Kaspersky recommends use of Application Startup Control component of Kaspersky Endpoint Security, which will prevent execution of the file with the name perfc.dat and block the execution of the PSExec utility (it is a part of Sysinternals Suite).
- Do not run open attachments from untrusted sources.
- Backup sensitive data to external storage and keep it offline.
If not subscribed to Kaspersky security solutions; here's what you should do
- All companies running Microsoft Windows OS: Windows XP or Windows 7 are advised to upgrade to security patch: MS17-010 immediately.
- If machine reboots and you see this message (see below), power off the system immediately! This is the encryption process. If you do not power on, files are fine, said Hacker Fantastic via Twitter.
- People are advised to use AppLocker feature of Windows OS to disable the execution of any files that carry the name "perfc.dat" as well as the PSExec utility from the Sysinternals Suite.
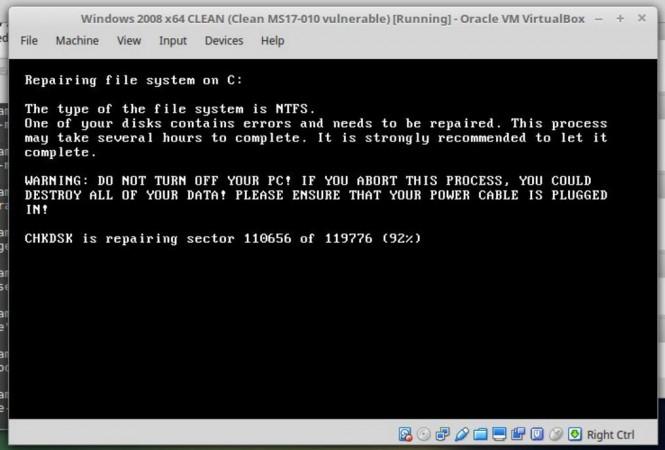
[Note: Once you switch off the system, make sure to disconnect internet connection. Turn on the PC and back up all your sensitive information in an external hard drive]
Watch this space for latest updates on cyber attacks and solutions.











