The safety of our digital lives has taken precedence as frequent cyber-attacks have raised some serious concerns. Even though tech giants and cybersecurity firms are hard at tracking loopholes that could be used to harm users, reports of security flaws being exploited by malicious gangs haven't slowed down.
As users fear their worst nightmares to come true, an alarming discovery has distressed millions of users. An Android vulnerability targeting bank accounts has been founded by the researchers at security firm Promon, which puts millions of users at risk of getting their bank accounts drained.
Who is at risk?
The vulnerability, termed StrandHogg, is hard to detect on an infected device as it disguises as a legit app. StrandHogg affects all versions of Android, including Google's latest security-focused Android 10. According to the researchers, top 500 popular apps are at risk of being exploited and Promon found 36 malicious apps exploiting the Android vulnerability.

What are the risks?
StrandHogg's exploitation capabilities on an infected device are alarming. The researchers note that hackers could access all private photos and files on the device, phone logs, location and GPS tags, contact list, listen to the user through the microphone, take photos using the camera, read and send SMS, make phone calls and record conversations.
But the scariest of all is the StrandHogg's ability to phish login credentials. This can result in gathering banking credentials, which can be used to drain users' bank accounts. The report puts more than 60 financial institutions in the crosshair of hacker's target. Promon found the dangerous Android flaw to be actively stealing money from bank accounts using malicious apps.
"It targeted several banks in several countries and the malware successfully exploited end-users to steal money. We'd never seen this behaviour before," Tom Hansen, the CTO of Promon, said in a statement.
How does it work?
The malicious app can mimic the legitimate app with an identical icon on the phone screen. The malware displays a fake screen and requests permissions, which appear to be coming from the legit app. If the victim grants those permissions without suspecting, hackers gain control to the device. To avoid suspicion, once the permissions are granted, users are directed to the legitimate app, so there's no way users can find out if they have been infected.
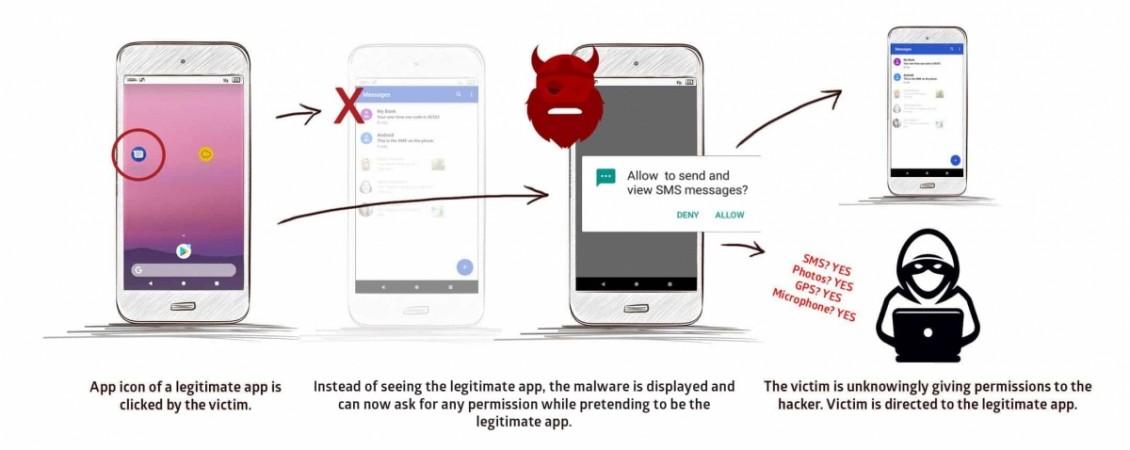
Similarly, a malicious log-in page is displayed on top of legitimate apps, using which hackers gather sensitive log-in information. This could include your social media credentials, or worse - your bank's online login details.
"We have tangible proof that attackers are exploiting StrandHogg in order to steal confidential information. The potential impact of this could be unprecedented in terms of scale and the amount of damage caused because most apps are vulnerable by default and all Android versions are affected," Promon CTO Tom Lysemose Hansen said.
Should you be worried?
Google was notified of the malicious apps exploiting the vulnerability and the search giant has removed them from Play Store.
"We appreciate the researchers' work and have suspended the potentially harmful apps they identified. Additionally, we're continuing to investigate in order to improve Google Play Protect's ability to protect users against similar issues," Google said, responding to the research findings.

But the risk hasn't averted. Researchers warn that the vulnerability still exists in all versions of Android. Unfortunately, Promon's research findings did not reveal the names of the infected apps, which means users have no way of finding if they are infected. Even though Google removed the apps from its app marketplace, users might continue to use apps if they are not made aware of the risks.
How to be safe?
As a precaution, users can check if the apps they use regularly are available on Play Store. Apps that are not in use must be cross-checked for their presence in the Play Store. Until Google patches the vulnerability, users are advised to practice caution while engaging with apps and permissions.
Users must always verify the name of the app asking for permissions and the kind of permissions (check for relevance to the app). Even though phishing pages appear identical, look closely for any mistakes in the UI. The buttons on phishing links do not work and when hitting the back button doesn't work as intended, it's a cue.
















