
GitHub encountered the largest-known DDoS attack in history earlier this week, but the developer platform's defenses set an example of how the world must react against such attacks.
The assault took place on February 28, and GitHub detailed the incident in a blog post dated March 1.
A DDoS attack — or distributed denial-of-service attack — is a common technique used by hackers and cybercriminals to take their targets offline. The cyber attack involves bombarding a website or an online service with so much traffic that it cannot handle it and crashes.
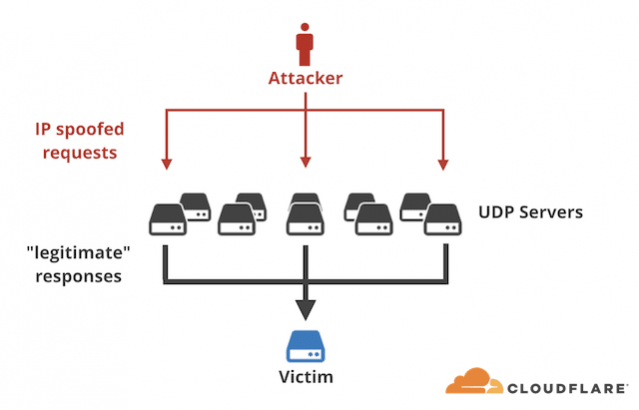
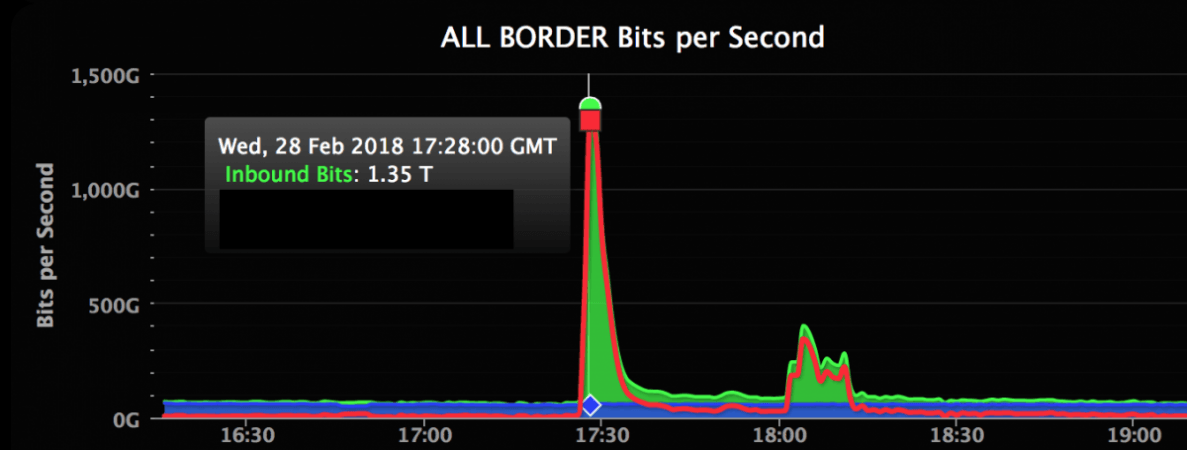
In the case of the GitHub attack, hackers injected traffic scaling up to a whopping 1.35Tbps at the peak — the highest-ever recorded. The hackers targeted a distributed memory system called "memcaching," which is responsible for increasing the speed on websites and networks.
Hackers had an advantage here as memcached servers are mostly exposed without proper authentication. By spoofing the victim's IP address, hackers can send small queries to elicit a much larger response.
In the case of GitHub's DDoS attack, the amplification attack spiked volumes by around 50 times, Wired reported. Due to the sudden rise in traffic on memcached servers, GitHub called for help from Akamai Prolexic, a DDoS projection provider, and quick thinking and implementation of strong defenses helped the security firm fend off the attackers in a matter of minutes.
Akamai implemented various techniques to fight off the DDoS attack, including rerouting traffic to its own servers and removing and blocking malicious data from the servers. The assault carried on for eight minutes and took down the GitHub website for 5 minutes between 6:21 pm to 6:27 pm (UTC).
"We modeled our capacity based on fives times the biggest attack that the internet has ever seen," Josh Shaul, vice-president of web security at Akamai, told Wired. "So I would have been certain that we could handle 1.3 Tbps, but at the same time, we never had a terabit and a half come in all at once. It's one thing to have the confidence. It's another thing to see it actually play out how you'd hope."
GitHub's 1.3Tbps DDoS attack is the highest ever recorded. The previous one in this range took place in 2016, during which the Mirai botnet bombarded a cloud server in France with 1.1Tbps traffic and infected tens of thousands of IoT devices.
GitHub said that at no point during the latest DDoS attack was there a breach of confidentiality or integrity of user data.
"We're investigating the use of our monitoring infrastructure to automate enabling DDoS mitigation providers and will continue to measure our response times to incidents like this with a goal of reducing mean time to recovery (MTTR). We're going to continue to expand our edge network and strive to identify and mitigate new attack vectors before they affect your workflow on GitHub.com," the official blog post noted.
Akamai warned that similar DDoS attacks are bound to happen and GitHub's 1Tbps assault won't be the biggest for long. Security firm Cloudflare has identified over 50,000 vulnerable memchached servers around the world, which are easy targets for DDoS attackers.
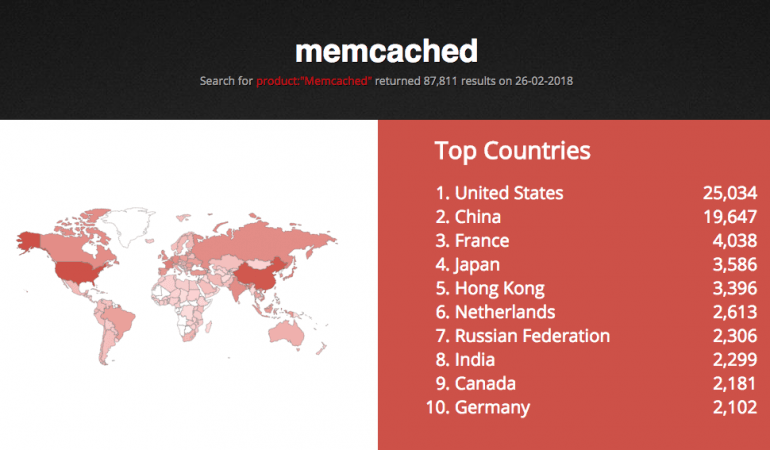
In preventive measures, Cloudfare advises organizations to disable UDP support the protocol is when not in use and also keep default enabling off. To strengthen security, it is best to firewall memcached servers in order to prevent the risk of DDoS attacks.













