
Researchers from Kaspersky Lab, a Moscow-based cyber security and anti-virus provider, have said in a report that it has discovered a highly sophisticated cyber-espionage campaign called Slingshot that spreads through compromised routers and remains undetected for years altogether.
Slingshot is as complex as Project Sauron, the malware that remained undetected for five years and believed to be designed by a state-sponsored group. Another malware, Regin, that infected computers in several countries including India remained undetected for several years.
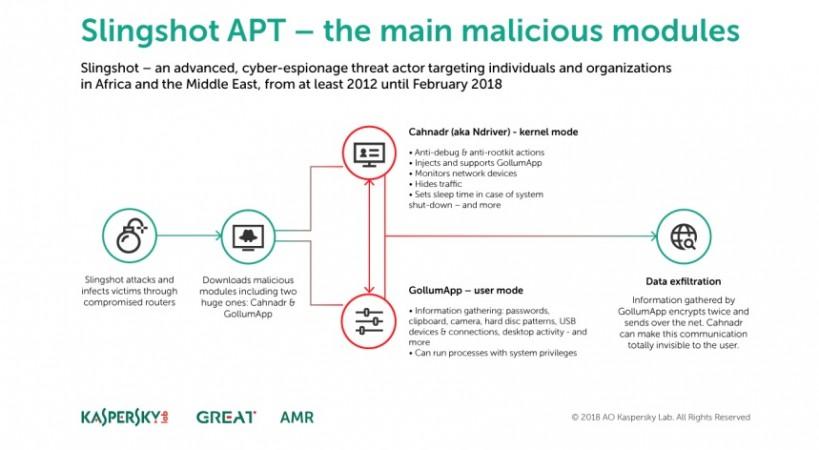
According to the researchers, there are almost 100 Slingshot victims, mainly from the Middle East and African countries. The threat is believed to have started in at least 2012 and is still active (February 2018). It went on to say that most of the victims initially got their computers infected through compromised Mikrotik routers or windows exploit.
The researchers said that a malicious code is found in several compromised routers made by the Latvian network hardware provider, making them believe that Slingshot is able to target victims by directly infecting such routers.
However, they are clueless about how exactly the Mikrotik routers are compromised.
"The discovery of Slingshot reveals another complex ecosystem where multiple components work together in order to provide a very flexible and well-oiled cyber-espionage platform," wrote Kaspersky Lab researchers in its report.
"The malware is highly advanced, solving all sorts of problems from a technical perspective and often in a very elegant way, combining older and newer components in a thoroughly thought-through, long-term operation, something to expect from a top-notch well-resourced actor," they added.
The malware can run in both kernel mode and user mode modules, which means attackers can have complete control over a compromised device.
How to avoid falling victim to Slingshot malware
Here are measures suggested by Kaspersky Lab researchers to keep advanced persistent threats (APTs) like Slingshot at bay:
- Upgrade your Mikrotik router to the latest software version. However, it said you can avoid only one attack vector with such updates and not from the APT itself.
- Implement a strategic approach to deal with attacks from the sophisticated malware. Security solutions like Kaspersky Threat Management and Defense can detect APT and come with expert services. If a targeted attack is detected, cybersecurity experts will act accordingly before any harm is done.














